Cyberstalking in Cyber Security refers to the use of the Internet and/or other electronic communications devices to stalk another person. It involves harassing or threatening behavior that an individual will conduct repeatedly, for example, following a person, visiting a person’s home and/or at a business place, making phone calls, leaving written messages, or vandalizing against the person’s property.
Cyberstalking has been defined as the use of information and communications technology particularly the Internet, by an individual or group of individuals to harass another individual, group of individuals, or organization. The behavior includes false accusations, monitoring, transmission of threats, ID theft, damage to data or equipment, solicitation of minors for sexual purposes, and gathering information for harassment purposes.
Table of Contents
Key Characteristics of Cyberstalking
- Harassment: Repeatedly sending unwanted messages, emails, or making phone calls.
- Threats: Using technology to threaten harm, either physically or emotionally.
- Invasion of Privacy: Monitoring or tracking an individual’s online activities or location without consent.
- Defamation: Spreading false information or rumors online to damage someone’s reputation.
Types of Cyberstalking
- Social Media Stalking: Monitoring a person’s social media profiles and activities.
- Cyberbullying: Using digital platforms to harass or intimidate someone, often targeting vulnerable groups.
- Doxxing: Publishing private information online to cause harm or distress.
- Phishing and Spoofing: Using deceptive tactics to steal personal information or impersonate someone online.
Statistics and Impact
According to a 2023 study by the Cyberbullying Research Center, approximately 7% of adults in the U.S. have experienced cyberstalking, with 46% of victims reporting significant emotional distress. The impact of cyberstalking can be severe, leading to anxiety, depression, and in extreme cases, physical harm.
Types of Stalkers
As the Internet, has become an integral part of our personal and professional lives, cyberstalkers take advantage of ease of communication and an increased access to personal information available with a few mouse clicks or keystrokes.
→ There are primarily two types of stalkers.
- Online Stalkers: They aim to start the interaction with the victim directly with the help of the Internet. E-Mail and chat rooms are the most popular communication medium to get connected with the victim, rather than using traditional instrumentation like telephone/cell phone. The stalker makes sure that the victim recognizes the attack attempted on him/her. The stalker can make use of a third party to harass the victim.
- Offline Stalkers: The stalker may begin the attack using traditional methods such as following the victim, watching the daily routine of the victim, etc. Searching on message boards/ newsgroups, personal websites, and people finding services or websites are most common ways to gather information about the victim using the Internet. The victim is not aware that the Internet has been used to perpetuate an attack against them.

Cases Reported on Cyberstalking
The majority of cyberstalkers are men and the majority of their victims are women. Some cases also have been reported where women act as cyberstalkers and men as the victims as well as cases of same-sex cyberstalking.
In many cases, the cyberstalker and the victim hold a prior relationship, and the cyberstalking begins when the victim attempts to break off the relationship, for example; ex-lover, ex-spouse, boss/subordinate, and neighbour. However, there also have been many instances of cyberstalking by strangers.
How Cyberstalking works?
It is seen that stalking works in the following ways:
- Personal information gathering about the victim: Name; family background; contact details such as cell phone and telephone numbers (of residence as well as office); address of residence as well as of the office; E-Mail address; date of birth, etc.
- Establish contact with the victim through telephone/cell phone. Once the contact is established, the stalker may make calls to the victim to threaten/harass.
- Stalkers will almost always establish contact with the victims through E-Mail. The letters may have the tone of loving, threatening or can be sexually explicit. The stalker may use multiple names while contacting the victim.
- Some stalkers keep on sending repeated E-Mails asking for various kinds of favors or threaten the victim.
- The stalker may post the victim’s personal information on any website related to illicit services such as sex-workers’ services of dating services, posing as if the victim has posted the information and invite the people to call the victim on the given contact details (telephone numbers/cell phone numbers/E-Mail address) to have sexual services. The stalker will use bad and/or offensive/attractive language to invite the interested persons.
- Whosoever comes across the information, start calling the victim on the given contact details (telephone/cell phone no’s), asking for sexual services or relationships.
- Some stalkers subscribe/register the E-Mail account of the victim to innumerable sex sites, because of which the victim will start receiving such kind of unsolicited E-Mails.
Real Life Incident of Cyberstalking
Case Study:
The Indian police have registered the first case of cyberstalking in Delhi — the brief account of the case has been mentioned here. To maintain confidentiality and privacy of the entities involved, we have changed their names.
Mrs. Joshi received almost 40 calls in 3 days mostly at odd hours from as far away as Kuwait, Cochin, Bombay, and Ahmedabad. The said calls created havoc in the personal life destroying mental peace of Mrs. Joshi who decided to register a complaint with Delhi Police.
A person was using her ID to chat over the Internet at the (particular website) for four consecutive days. This person was chatting on the Internet, using her name and giving her address, talking in offensive language. The same person was also deliberately giving her telephone number to other person who were online encouraging them to call Mrs. Joshi at odd hours.
This was the first time that a case of cyberstalking was registered. Cyberstalking does not have a standard definition but it can be defined to mean threatening, unwarranted behavior, or advances directed by one person toward another person using Internet and other forms of online communication channels as a medium.
How to Protect Yourself from Cyberstalking
Protecting yourself from cyberstalking involves a combination of practical measures, digital hygiene, and vigilance. Here’s how you can minimize the risks:
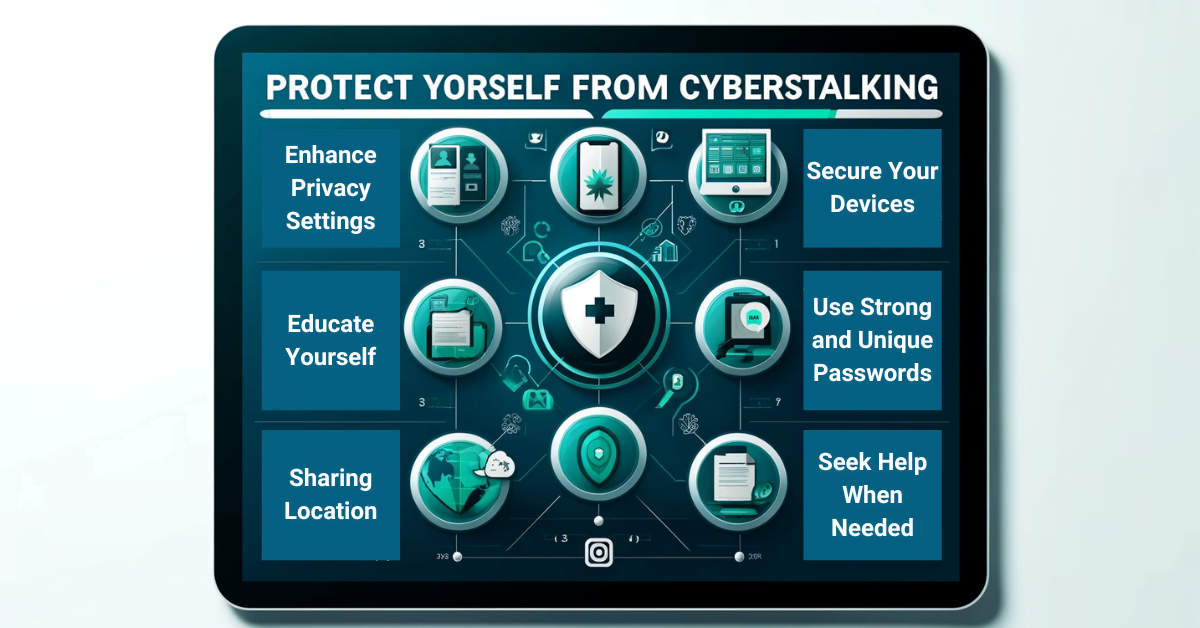
- Enhance Privacy Settings: Adjust the privacy settings on all your social media accounts to limit who can see your posts and personal information. This can include details like your birthdate, email address, phone number, and physical address.
- Use Strong, Unique Passwords: For all online accounts, use strong, unique passwords. Consider using a password manager to keep track of different passwords for different sites. Enable two-factor authentication (2FA) wherever possible to add an extra layer of security.
- Sharing Location: Be cautious about sharing location information online. This includes geotagging posts with your location on social media and location sharing services.
- Secure Your Devices: Ensure that all your devices are secured with passwords, fingerprints, or other biometric locks. Keep your operating system, antivirus software, and apps updated to protect against vulnerabilities.
- Keep Personal Information Private: Be mindful of the personal information you share online. This includes avoiding posting things that could give away your location, routines, or plans. Also, be cautious about who you accept connection requests from on social media.
- Monitor Your Digital Footprint: Regularly search your name on search engines and social media to see what information is publicly accessible about you. This can help you understand what a potential stalker might be able to find out.
- Be Careful with Communication: If you receive suspicious or unsolicited messages, do not respond. Block the sender and report them to the platform if possible.
- Educate Yourself on Cyberstalking Laws: Know the laws in your area regarding cyberstalking. This can help you understand your rights and the steps you can take if you believe you are a victim of cyberstalking.
- Document Suspicious Activities: If you suspect that you are being cyberstalked, keep a record of all suspicious activities, including dates, times, and details of the incidents. This documentation can be useful if legal action is necessary.
- Seek Help When Needed: If you feel threatened, consider contacting local authorities or seeking help from organizations that deal with cyberstalking or online harassment.
By Implementing these strategies you can significantly improve your defenses against cyberstalking, helping you maintain your privacy and safety online.
Related Articles
Read about these articles and keep yourself updated about the latest cyber security trends.
